Understanding VPNs: A Simple Tool with a Complex Role
 Virtual Private Networks, or VPNs, have been in the news a great deal in recent years, however, it’s rarely been in a positive light.
Virtual Private Networks, or VPNs, have been in the news a great deal in recent years, however, it’s rarely been in a positive light.
Most recently, attention has been placed on Netflix after many users began to complain that they were unable to access the site via VPNs. Netflix has denied that it’s targeting VPNs especially, but that it continues to say VPNs are against its terms of service.
The issue centers around the ability of VPN users to appear as if they are visiting from another location, making it possible for viewers outside the United States, for example, to get access to U.S. exclusive content.
But while VPNs are relatively simple tools to understand, their role on the Web is significantly more complex. There are many uses for a VPN, some of them are good, some of them are not. But no matter what your role is on the Web, it’s worth taking a moment to understand what a VPN is, how it works and what the limitations of a VPN are.
Once you understand what a VPN is, it becomes easier to talk about their function and the people who use them, whether for good or for ill.
The Basics of a VPN
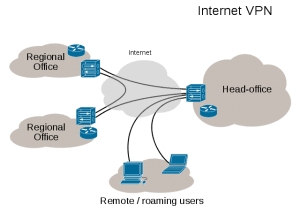 When you connect to the Internet, whether it’s at home or on the road, generally you are connecting to a router close to you, which is connected to your ISP, which connects you to the broader Web.
When you connect to the Internet, whether it’s at home or on the road, generally you are connecting to a router close to you, which is connected to your ISP, which connects you to the broader Web.
The problem is that a lot of your Web traffic isn’t secured. This means that anyone on your network or at your ISP can observe what you’re doing. Also, any sites that you visit will have your real IP address, the number used to identify your computer on the Web. Along with that, the site will likely know your city, country and other information that could be used to identify you.
When you use a VPN, you are creating a secure connection between your computer and a VPN server located somewhere else. As one VPN provider puts it, the VPN server becomes something of a PO box for you on the Internet, receiving your data and forwarding it to you, but in a way that can’t easily be traced back to you.
If you are connected to a VPN and request a Web page. Your computer uses the secure channel to instruct the VPN server to download the content. The VPN server then goes out on the Web, pulls down the Web page content and sends back the data using the secure connection you have with it. As a result, all data going to and from your computer is encrypted and to the page you visited, it looks like the VPN server, not your computer, is the end user.
VPNs have been around for decades and actually got their start in corporate security and government security. Even during the dial up days, many corporate employees, if they wanted to work from home, would have to connect via a VPN before they could access internal company servers, to ensure that nothing along the line could snoop on the connection.
Today, many companies enforce similar rules, which have become even more important with the proliferation of open wifi connections and other unsecured connections. However, what has changed in more recent years is the rapid growth in popular of VPNs for general web surfing, a shift that has caused VPNs to run into controversy for their role in copyright infringement and other legal violations.
The Uses of a VPN
There are a lot of reasons one might want to use a VPN, but the more common ones are as follows:
- Secure Local Connection: Anyone snooping on an open wifi, on your network or at your ISP will not be able to see what you’re doing or snoop your data in transit.
- No Geolocation: It’s relatively easy to use an IP address to find a rough geographical location. A VPN prevents that and allows the user to appear to be from wherever their VPN server is located.
- No Real IP Address: No site or computer you visit while on a VPN will have your real IP address.
- No Throttling: If your ISP throttles or limited some services, encasing all of your data in a VPN makes it look identical, ensuring that it is all treated the same. Regardless of if it’s VOIP, streaming music, etc.
- Additional Security Benefits: Some VPN services provide additional security benefits, such as blocking risky sites or parental controls. They can also force you to use a secure domain name server (DNS), preventing various DNS-related attacks.
The big drawback to a VPN is the trust that you’re putting into it. While your ISP and local network can no longer collect data on your traffic, your VPN provider certainly can. In fact, your VPN company has the theoretical ability to snoop and record all of your Internet traffic.
This has raised the issue of VPN anonymity and, in particular no-logging VPNs. The idea is straightforward, the less information about you VPN provider keeps, the more anonymous you are.
The other drawback is that VPNs do add a layer between your computer and the Internet and, with it, performance will suffer. Though it might be difficult or impossible to see, passing your connection through more servers will not speed up your connection, unless you are bypassing throttling.
For many though, the small performance hit and questions about privacy on the VPN side outweigh the risks of not using a VPN, prompting them to pay $5-$10 per month for the privilege (or at least use a free alternative).
However, it’s what the users have done with those VPNs that have drawn the most controversy.
Common Uses of VPNs
VPNs have a lot of benefits and, with those benefits come a great deal of uses. Many of those uses have been very positive including:
- Securing Insecure Connections: Coffee shop, airport and hotel wifi points can be very convenient, but they can also be very bad for security as, in many cases others can view what you send not it. Also, if the network itself wants to snoop, it has the ability to record and log everything sent through it.
- Circumventing Censorship: As countries such as Egypt began cracking down on Internet access, many citizens used VPNs to bypass government controls.
- Bypassing Throttling: When Verizon was accused of throttling Netflix, one user used a VPN to bypass the throttle and prove that Verizon was manually slowing the service down.
- Protect Privacy: If you’re doing something such as sending DMCA notices to infringing sites, a VPN can help guarantee that your real IP address is never in the hands of a potential attacker.
On the other hand, VPNs have been used for a lot of less savory activity too. The same privacy and security tools that are useful to legitimate users also serve well copyright infringers and others committing unlawful acts online.
- Bypassing Geolocation: VPN users can bypass geolocation restrictions, such as with YouTube and Netflix, that prohibits the viewing content not licensed for their country.
- Evading Copyright Enforcement: Using a VPN while engaging in piracy means that your real IP is never exposed to any potential copyright enforcers, making it harder to track infringers down.
- Hiding Criminal Activity: Whether buying illegal goods online or hacking into a corporate system, most who are committing a crime online will use a VPN to add a layer of protection and anonymity to their activities.
- Circumventing IP Blocks: If a user is blocked on a forum, (Spamming, Trolling etc.) or is blocked for abusing a resources (Too many password guesses, etc.) a VPN is a quick way to get a new IP address and try again.
So, while VPNs have certainly found a lot of legitimate uses, they’ve also been used more than a few times for unethical or unlawful acts.
But this in turn asks another question, whether you are using a VPN for good or evil, how secure is it?
A Word on VPN Security
As with just about anything to do with security, the security of your VPN is going to depend on how you use it, what you do with it and who is trying to break your security.
For example, any decent VPN will likely protect a casual user worried about snooping while on a hotel wifi. However, if you’re a hacker trying to use a VPN to attack a major corporation or a government, it’s unlikely you’ll find any VPN provider to be a very safe place.
That is what Cody Kretsinger learned in 2011 when he was arrested for taking part in the hacking group LulzSec. Kretsinger had used the VPN service HideMyAss and the U.S. government was able to get a court order for the service’s logs. Though the company was only able to provide limited logs, it was enough locate and arrest him.
Competitors of HideMyAss, as well as privacy critics, jumped on the company for keeping the logs at all. However, HidaMyAss responded saying that the logs were necessary to stop those who were abusing the system.
But even VPNs that keep no logs are not completely safe. Recently leaked documents show that the NSA has had the ability for years to decrypt and access some VPN traffic.
Evidence of this has piled up elsewhere, in particular on Tor, which functions much like a VPN but with multiple stages. In 2013 the U.S. government shuttered the first Silk Road, a notorious black market on the Tor network, and a large number of TOR-operated sites also went down. In 2014, the successor, Silk Road 2.0 was also closed and its operator arrested.
As HideMyAss said in its responses, it’s ridiculous to think that paying a few dollars per month gives you immunity from any crimes you commit on the Internet. Any activity done through a VPN can be discovered, it’s only a matter of the willingness and resources to do it.
Bottom Line
A VPN is a tool. It isn’t a magical tool to remove a person from all consequences and it isn’t a weapon only used for evil. It’s a tool that has things it is good for, limitations that hold it back, positive applications and negative ones.
When talking about VPNs, it’s important to remember just how complex and nuanced their place on the Web is. While they can be used as cover for unlawful acts, they are also needed protections for legitimate ones.
There’s simply no broad brush that one can paint VPNs in. In copyright, both copyright enforcers and those hiding from them make wide use of VPN technology.
As with so many things, there’s no tale of good or evil here, just a tale of people and they are both wonderful and flawed at the same time.
Credit: VPN Diagram by Ludovic.ferre, posted at Wikimedia Commons and Licensed under a Creative Commons BY-SA 4.0 International license.
Want to Reuse or Republish this Content?
If you want to feature this article in your site, classroom or elsewhere, just let us know! We usually grant permission within 24 hours.
